Back in 2016, one of the largest ad fraud rings ever was discovered by security researchers at WhiteOps. Now, another group of researchers have found what they believe to be the biggest ad fraud ring since the famous Methbot.
Known as Hyphbot, this sophisticated ad fraud ring has gone under the radar for several months before finally being discovered. Upon discovery, researchers estimated that the operation was costing advertisers over $200,000 a day and generating the group around the same in fraudulent profits. Now the operation has finally been revealed we can take a look at how the ring was set up and how they managed to fool everyone for so long.
In this article, we’ll be taking a look at the history of Hyphbot and how it grew into one of the most prominent ad fraud rings to date. We’ll also be exploring what gave the whole thing away, and what advertisers can learn from this huge discovery.
To get things started, let’s take a look at how Adform discovered this colossal fraud ring in the first place.
How Hyphbot Was Discovered

Hyphbot was originally discovered when Adform’s in-house algorithms started to pick up some unusual traffic activity. We don’t know exactly what they were looking for or tracking, but alarm bells began to go off at Adform HQ in 2017. This led to a full-scale investigation by the team that managed to unravel the entire Hyphbot network.
The story started when Adform investigated traffic sold by non-legitimate sellers by analysing where the traffic was coming from. During the analysis, Adform noticed some unusual URL structures that included random patterns of words. These URLs were presented as high authority sites such as Forbes and the Economist, but in reality, they were all fake.
To make things even more interesting, all the URLs used didn’t actually lead anywhere. In fact, they all lead to 404 pages which only confirmed Adforms suspicions even more. To explain it in simple terms, websites were buying what they believed was traffic to their site. In reality, this traffic was actually coming from a vast bot network of individual “zombies”.
To understand what a botnet is, we first need to explore how one works. For those not so technical readers, a botnet is basically a network of bots, hence the name. To build a botnet, a group of malicious hackers deploy malware to thousands of computers around the world.
This, in turn, gives them an army of “zombies” or “slaves” at their control. Once the botnet has been built, the owner can do anything they want with the computers. This includes telling them to visit a particular website or request information from another computer. Usually botnets are used to conduct DDOS (distributed denial of service) attacks, but in this case, someone found a way to make them much more profitable.
In their analysis, Adform found that the network had over 500,000 IP addresses just from the US alone. Since US traffic is commonly the most expensive type of traffic, this meant the group could make a lot of money selling it to advertisers.
With all of these slaves at their control, Hyphbot could fake thousands of traffic to all kinds of premium websites. With unaware advertisers paying up to $14 per 1000 impressions, that’s a lot of money lost to fraudulent views.
After discovering the fraudulent traffic, Adform worked with cybersecurity researchers to produce a white label paper on the fraud ring. By sharing this information with advertisers and ad networks, they can use the information collected to improve their fraud defenses.
So how exactly can advertisers and networks protect themselves from new attacks in the future?
What Can We Learn From Hyphbot?
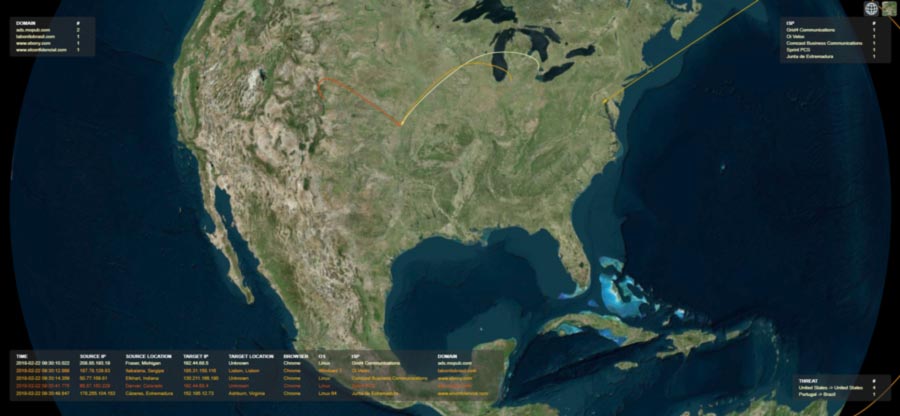
Thanks to Adform’s efforts of discovering and documenting Hyphbot, there are plenty of things advertisers and networks can learn from Hyphbot. From the structure of the fraud ring, to the browser used in the attack, all of this information is crucial in helping discover new fraud rings.
It also allows networks increase their fraud detection software that in turn helps increase the quality of their traffic.
In this discovery, the fake URLs played an important part of discovering the whole operation. These fake and fraudulent URLs were made to look like real websites, when instead none of the pages actually existed. This form of traffic spoofing was also seen in the Methbot operation where advertisers thought they were buying premium traffic. In reality, they were buying millions of bot visits to their sites instead.
This type of ad fraud is becoming increasingly popular and more common over the past few years. The chances are fraudsters will be using this type of fraud again in the future with a new twist to go undetected. By having an idea of the strategies and techniques fraudsters are using, other researchers can use these to help their own research efforts.
Protect Your Ads From the Next Hyphbot
Hyphbot might have already been exposed to the advertising world, but there are still plenty of other large-scale fraud operations out there. With fraudsters setting up new operations every single day, making sure your ads are protected from these criminals is vital.
Here at Lunio, we offer all users the best protection from click farms, click bots and annoying competitors. With our real-time analysis on every click of your advert, you can feel safe knowing you won’t be receiving any fraudulent clicks.
Backed by our extensive IP blacklist, we’ll also protect your ads from VPNs, repetitive clicks, and large-scale fraud rings.
Available from only $29 a month, Lunio is the only service you’ll need to protect your ads. To see how much money you can save on your AdWords campaigns, click below to try our free trial.


