It’s no secret that Facebook has had its fair share of ad fraud schemes over the years, and it’s often advertisers who bear the brunt.
Recently, Facebook has revealed details about an ad fraud scheme that has cost Facebook users millions, with most of the victims having never run an ad before.
Known simply as SilentFade, this silent and secretive malware has compromised thousands of Facebook accounts and has cost users up to a combined $4 million.
In a presentation at a cybersecurity conference, Facebook’s security team released the details of the malware and how it was able to compromise users accounts and run ads without their knowledge.
In this article, we’ll be taking a look at how it infected users, what the overall aim of the malware was, and how Facebook tackled this malware problem.
WTF Is SilentFade?
SilentFade is an internal name the team at Facebook used when investigating a suspicious piece of malware back in 2018. The name is short for “Silently running Facebook Ads with Exploits”, but SilentFade sounds a lot catchier!
Unknown to them at the time, the gang behind the malware had been around since 2016, making various Facebook malware to infect users. One of their first malware programs was called SuperCPA and was primarily targeting Chinese users.
Although not a lot is known about the SuperCPA malware, the team concluded that it was related to click fraud activity. And it was most likely designed to increase the CPA (cost per acquisition) of competitor’s ads by continually clicking on them.
Shortly after in 2017, the team stopped making SuperCPA and made their first version of SilentFade. Over the next couple of years from 2017 to 2019, the team released various new versions of the malware, each one becoming more dangerous and advanced.
In its final form, the malware took advantage of a bug in Facebook’s platform and through browser injection, it was able to compromise and take over user’s accounts.
Once the malware had access to Facebook accounts, it would check to see if they had any payment options attached, such as pre-saved credit card details. If the account did have payment details attached, then it would start to run Facebook ads using the victim’s funds.
These ads would often use blurry and distorted pictures of celebrities and fitness models to sell shady products such as diet pills, fake designer sunglasses, and other fitness products. Once the ads were live and running, they looked like this:
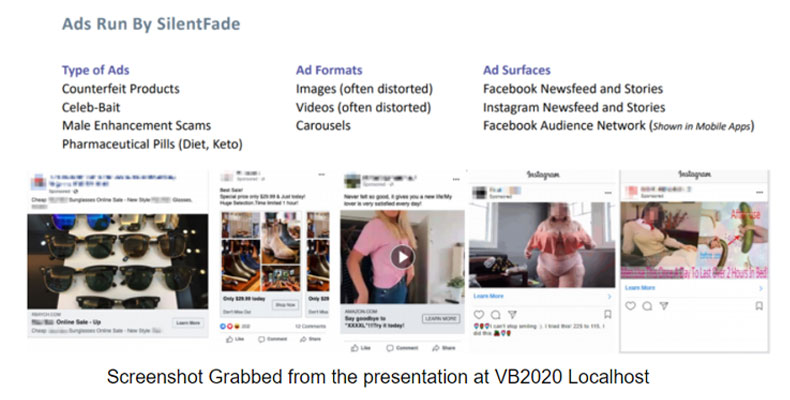
Every time they received a click from other users, the victim would be charged without even knowing. The malware also disabled Facebook’s notification alerts that alerted the user when their ads were approved and went live. This significantly helped evade detection from users and in most cases, helped extend the duration in which they were infected.
It’s only after many weeks and many clicks when Facebook finally took the payment from their payment method that many of them realized something was wrong. Considering almost all of the users had never run Facebook ads before, being charged by Facebook for running ads on their platform obviously triggered alarm bells.
Although no credit card or bank details were exposed to the hackers, the fact that they could still use the Facebook API to charge them is a huge exploit.
How SilentFade Spread

According to Facebook’s security team, SilentFade was spread by being bundled with pirated versions of software, such as Coreldraw and similar products. Although none of these files were initially downloaded from Facebook, they quickly managed to infect any user who installed them.
Usually, files like these are found on file-sharing websites such as torrent trackers where it is easy to hide infected files. Many unsuspecting users download and install these files without ever checking them for malicious malware or viruses.
Once the file was installed on the victim’s computer, it began to steal autosaved credentials and cookies from browsers including Chrome, Firefox and Internet Explorer. This meant that anyone who stayed logged into Facebook for days without logging out had their account easily compromised.
Unlike account credentials, cookies store plenty of sensitive information including session tokens which bypass many protection systems, such as two-factor authentication. This meant that any cookie they managed to steal from users gave them full access to the Facebook account without having to brute force their way in.
Another reason why remembering to log out is important in today’s age!
Facebook’s Response

In response to the malware threat and to ensure users they are being proactive in stopping new attacks, Facebook launched a full investigation into the malware.
The first thing Facebook did is they identified all the users who were victims of the SilentFade malware and issued them refunds. By their estimates, the refunds added up to just over $4 million and dated back several years to 2018.
After examining the malware and testing it on sandbox computers, they also identified the main Facebook platform bug it was exploiting, and immediately fixed it. They also explored the other browser injection exploits it took advantage of and informed browser developers on how they could be fixed.
During their investigation, Facebook also identified several other malware campaigns, including StressPaint, FacebookRobot and Scranos, some of which are still active today. Although not much is known about these aside from them being similar malware programs, Facebook ensured users that deactivating them is their top priority.
Their security team also stressed that cybercrime is definitely on the rise, and they fully anticipate more Facebook malware to appear over the upcoming years. But by educating users and other security professionals on the types of malware they are facing, they hope everyone can work together in detecting and eliminating new threats.
The Dangers Of Managerial Access

This whole malware story just goes to show how user privileges can be exploited without the user knowing before it’s too late. And it’s not just Facebook who are open to this kind of attack.
The same type of attack can happen to anyone with a Google Ads account who gives another user managerial access.
If the user or agency who has managerial access to your account gets their account compromised, then you’ll also be affected. This means whoever has access to their account will also have access to your account and could create their own ads to waste your money.
By giving anyone full managerial access to your account, you’re putting a lot of trust in their hands which can often backfire. And if one account has several or even hundreds of other accounts attached to it, they can often become a big target for hackers.
Why try and hack 50 individual Google Ads accounts, when you can just hack one that has full managerial access to all the rest?
The next time an agency or third party tool asks for full managerial access to your account, ask yourself, do they really need this level of access? In most cases, they can often operate with limited access or API access (for 3rd party tools) which significantly reduces the chances of them making unauthorized changes to your account.


